DROWN security threat
Janus Network Security customers should be aware of a security threat known as the "DROWN attack" (https://drownattack.com/). The DROWN threat exploits a security vulnerability of network SSL ports that use SSL V2.
DROWN (Decrypting RSA with Obsolete and Weakened eNcryption) allows an attacker to decrypt intercepted TLS connections by making specially crafted connections to an SSL V2 server that uses the same private key.
As stated in the detailed recommendations below, under Model 204 7.5 and later, exposure to this DROWN attack is eliminated because SSL V2 support is disabled. The best solution to the DROWN attack is to upgrade to the latest release, Model 204 7.6.
Recommendations
The DROWN threat exploits a security vulnerability of SSL ports that use SSL V2. In response, the Rocket M204 security team has the following recommendations:
1. Disable SSL V2 (Model 204 7.4 and lower)
- On Model 204 7.5 and later, SSL V2 support is already disabled.
- On an older version of Model 204, set the Janus port parameter SSLPROT to X'1E' on all Janus SSL ports. This disables SSL V2. The SSLPROT default for these versions is X'07'.
- Make sure that Janus ports do not share certificates with any other ports that support SSL V2. Even ports that do not support SSL V2 are vulnerable to the DROWN attack if they share certificates with ports that do.
It is also strongly recommended that you upgrade to Model 204 7.6 as soon as possible.
2. Disable SSL V3 (all Model 204 versions)
While SSL V3 is not considered a major security exposure, Rocket Technical Support recommends also disabling SSL V3.
To do this, specify one of the following settings on all Janus SSL ports:
- Recommended, if possible in your environment: Set SSLPROT X'10', which only allows TLS 1.2. (The drawback to this approach is that quite a few SSL clients still do not support TLS 1.2.)
- Next best alternative: Set SSLPROT X'18', which disables TLS 1.0.
- Or, set SSLPROT X'1C', which allows only TLS 1.2, 1.1, and 1.0.
The problem with SSL V3
SSL V3 has been known to be a security risk since 2014 (see Google Security Blog article).
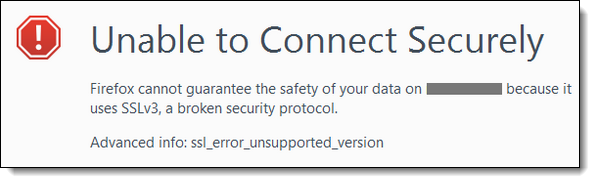
By default, some browsers may not support SSL V3. Currently, when using the FireFox browser, if your connection requires SSL V3, you may get an error like the following:
The discussion of this error is found on the Mozilla support pages.
After SSL V3 is disabled
If an application needs SSL V3 and a Janus port has disabled it, Model 204 will reject the connection and return the following error to the browser:
MSIR.0573 SSL client trying to use unsupported protocol: protocol
The message means that a client (probably a web browser) tried to connect to an SSL port, but it tried to use an SSL protocol that is explicitly blocked by the SSLPROT parameter in the JANUS DEFINE command.
See also
For more technical information about the DROWN attack, see: https://drownattack.com/drown-attack-paper.pdf
If you have further questions about this DROWN issue, contact Rocket Technical Support at Support@RocketSoftware.com.